Today, a colleague of mine came with an interesting question: how can I search & replace a string with the content of a file. I naturally tought to vim.
I started digging, but couldn’t find a direct way to do it. So, I decided to use a named buffer to hold the content file.
So let’s say that you are editing a file A (current buffer) and want to replace all occurences of MyOldString with the content of MyOtherFile.txt.
Here is the way to do it:
While editing your file, type the following commands:
:edit MyOtherFile.txt
gg"ayG
:bdelete
:%s/MyOldString/\=@a/g
Some explanation:
:edit MyOtherFile.txt This command creates a new buffer and open the file MyOtherFileFile.txt.gg Go to the top of the file."a Use named buffer ayG Yank (y) all text (G):bdelete delete the file buffer (MyOtherFile.txt) and go back to the original file:%s/MyOldString/\=@a/g search the whole file (:%s) for the string MyOldString and replace it with the content of named buffer (\=@a) for all occurences (g).
This is quite usefull in some case. This could be transformed in a named macro…
Any other method to vim search & replace string with a file content (or without viw) is welcome.
Share your thoughts
In september 2015, I published an article on LinkedIn about IPv6 because ARIN announced that they have exhausted their IPv4 address space! I think that we will, finally, see a lot of enterprise adopting IPv6.
The North American organization is now only able to deliver very small chunk of IPv4 addresses for help in transitioning from IPv4 to IPv6.
First of all, IPv6 is not a new protocol. IETF is working on this since 1990s.
IPv4 is (was?) 32 bit address space, with a lot of unusable IP addresses (Test, Multicast, Reserved for ?Future Use?, Network address, Subnetting, …). The theoretical maximum number of addresses is 2^32 (4294967296). In IPv6, the maximum number of addresses is 2^128 (340282366920938463463374607431768211456 or 3,4*10^39).
Most modern systems are able to run dual stack (IPv4 and IPv6), as are most modern application.
While IPv6 is still IP in the payload and the general behaviour, the way to use, route and allocate addresses is totally different than IPv4.
First of all, about address allocation. The system administrator should be able to forget everything he knows about IPv4 address allocation. In IPv6, you NEVER subnet in less than /64 networks (I wrote NEVER, this is NEVER). This is the most difficult part for Net and Sys admins. They must learn a new way of thinking. The idea behind this is to give a public IP address to all connected devices (nice for IoT).
The general routing protocol between the ISP is still BGPv4, but if you were using OSPFv2 for internal routing, you’ll have to use OSPFv3, right now.
The way the headers are organised in IPv6 reduce routers load.
Quality of servvice as Security were also built from the beginning in the protocol. In fact, IPSEC was defined for IPv6.
There are working, standardised discovery and autoconfiguration protocols to help the administrator to set-up his basic IPv6 Network.
So a tight integration with your DNS will be mandatory as 128 bits of IP addresses makes impossible to learn/remember all your important devices IP addresses like you (probably) did with IPv4. Therefore, a good working DNS infrastructure will be needed.
If I see that there is an interest in this short introduction, I’ll give a more detailed introduction on the working internals of IPv6 for SYS and NET admins!
You can also find a lot of information on http://ipv6actnow.com.
Pascal Fuks has achieved the HE certification of “IPv6 Sage” while he managed to drive his former company, Financial Art, to 4 stars at RIPE classification on companies implementing IPv6.
1 Comment
As previously explained, I had as part of a customer’s mission to propose a solution to accelerate a web site. The challenge was to replace an aging Juniper appliance by a reverse proxy for high trafic website. This appliance was accelerating the traffic by caching data (max. 100Mb), and balancing the traffic between 4 front end servers. I also wanted to reorganize the whole DMZ infrastructure to improve the security. The existing architecture had all servers (front-ends, database and application servers) in the same LAN behind the firewall and the Junipers (see HLD image for As-Is solution below).
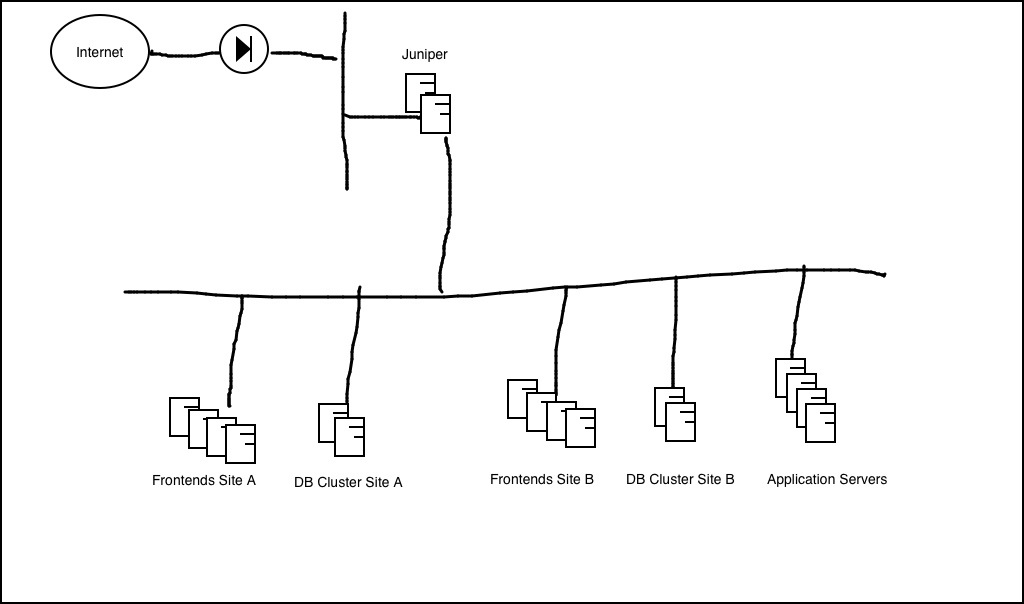
As-is solution
Don’t laugh, those websites receive more than 45.000.000 visits per month, with more than 4 pages seen at each visit (in normal traffic) and expect to receive more than 100.000.000 visits a month on special occasions. So, to improve this, I decided for a classical layered system (see HLD To-be solution below). Read the rest of this entry »
2 Comments
Hello to all my readers,
Those end of year (and beginning of year) activities kept me away from my computer.
I want to wish to all of you a happy new year 11111011101.
I’m taking a bit long to write my next post because I’ve got to prepare a brand new course on Cloud Computing Solutions for people learning how to become ICT Coordinators.
Hoping to read you soon and getting back next week.
Pascal
Share your thoughts
Hello,
This is a quick post to detail my coming articles. In the following days, I’ll post articles about:
- Varnish, a reverse proxy that I’m using in different projects. I’ll describe the functionalities and usages for this server, and will detail a CentOS 6 (RHEL) install.
- RHCS3 (Red Hat Cluster Suite 3), the clustering environment from Red Hat (and present in CentOS), and how to set it up for different purposes.
- A Varnish Resource Agent for RHCS3 that I wrote, to make Varnish cluster aware.
- A Varnish module that I wrote to add some functionalities in Varnish when used, mainly, with the Client Director (mainly a client identity base on IP and Port, as port information is missing in standard Varnish program)
- An implementation of Yubikey to create Cisco VPNs
- …
And I’m also waiting for your suggestions, and will be happy to answer your questions.
And now, I’ll wish you all the best for 2013…
Share your thoughts
A few years ago, I bought this domain name, just in case …
I thought about publishing a blog with IT tips and tricks of my own. It took some time to start this project. I was to lazy (I’m just working 75 to 100 hours a week) to bring the server on line, choose a blogging platform and finally write my first post.
First of all, a few words about me (be.linkedin.com/in/pascalfuks/): My name is really Pascal Fuks, it’s (unfortunately) not a joke (it’s just FOX in german with a spelling mistake – FUCHS). I did start to build and play with computers around 1979. In those times, one of my hobbies was electronic. In my magazines, they began to write about digital electronic (vs. analogic), and I wanted to try those things. I had an Altos computer (the one that was used to create CP/M), and builded a few things around microprocessors (SC/MP, 6502, 8080, Z80, 6809,…). I did also convince my school to buy a computer (TRS80-Model 1) and started a computer club in the school. After that, I did work with computers for companies during nights and weekends, while being still at school. I had the opportunity to work for Schneider/Amstrad (among others). I did develop what should be on of the first dongles in the computer history (first for the commodore 64, then for the Amstrad CPC). I did also wrote BIOSes, work on Wang computers, wrote the first ODBC driver for DB2 running on mainframes (1993), and a lot of other funny experiences. I had my first contact with Unix in 1987. It was a real revelation. Linux caught me around 1992 (early stage), but I did also wrote the first driver for the Creative 3dFX graphic card for Windows 2000 (you can still find it by googling for it). This illustrate my main aspect about IT: “There are a lot of solutions to achieve some goal, some of them are proprietary, some of them are open source, and they have all advantages and drawbacks. It just depend on who is using them and how”. I’m against trolling about what’s best or not. I like to find a good way to give my customers (http://www.financialart.be) the best results without sticking to products.
Anyway, there is only one religion: “Fear Murphy’s law!”, and my favourite sentence is
“When you’re in trouble, if you think it can’t be worse, you just lack imagination”.
“Both optimists and pessimists contribute to society. The optimist invents the aeroplane, the pessimist the parachute.” (G. B. Shaw)
Now, feel free to contact me (0473 818 007), and I’ll start to post interesting things I did develop, or just managed to make working, in my fascinating “Network & Security Architect” working life.
1 Comment
